Quantum-Resistant Cryptography Adoption: A 2026 ImperativeQuantum-Resistant Cryptography Adoption: Securing the Future
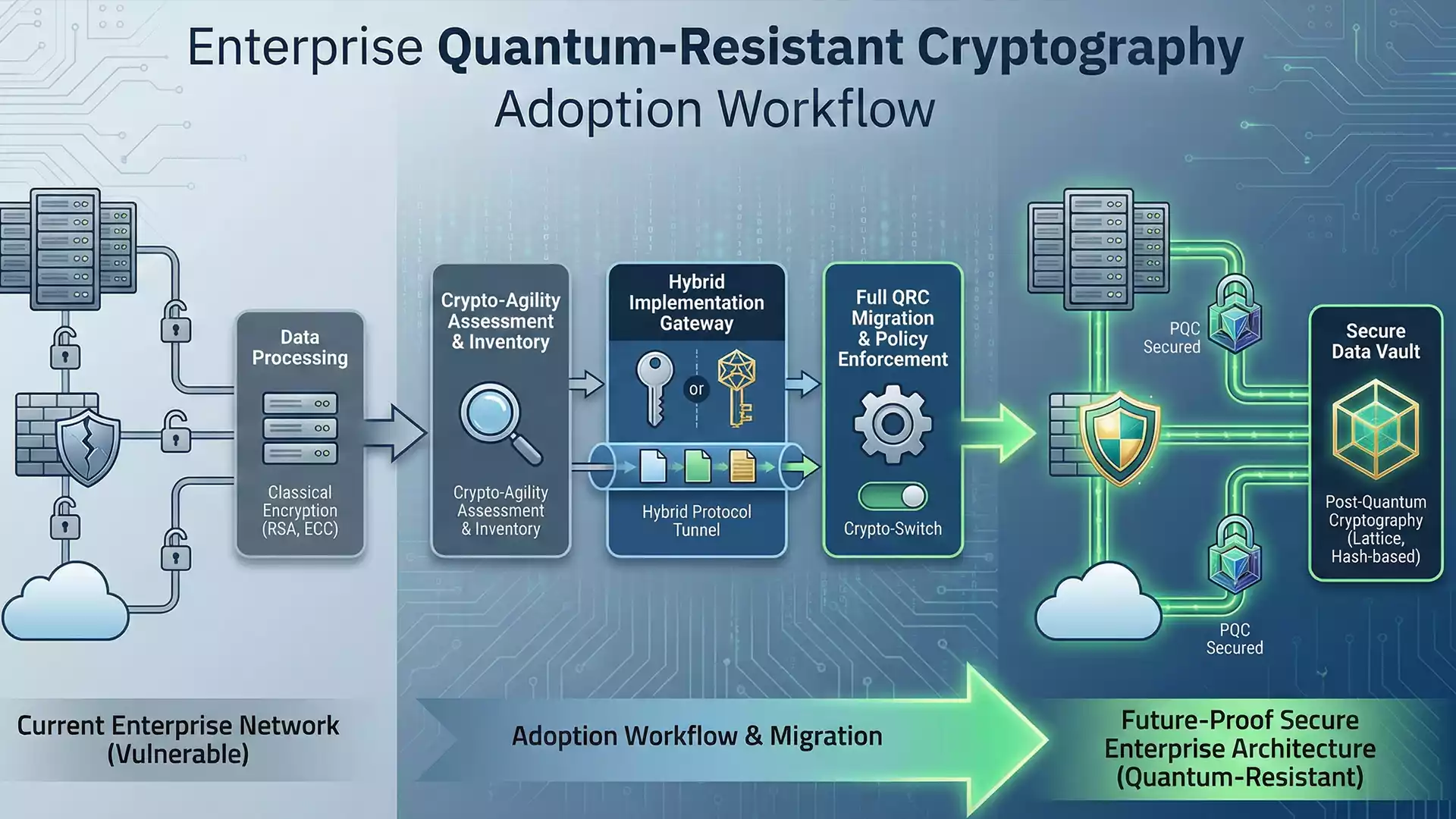
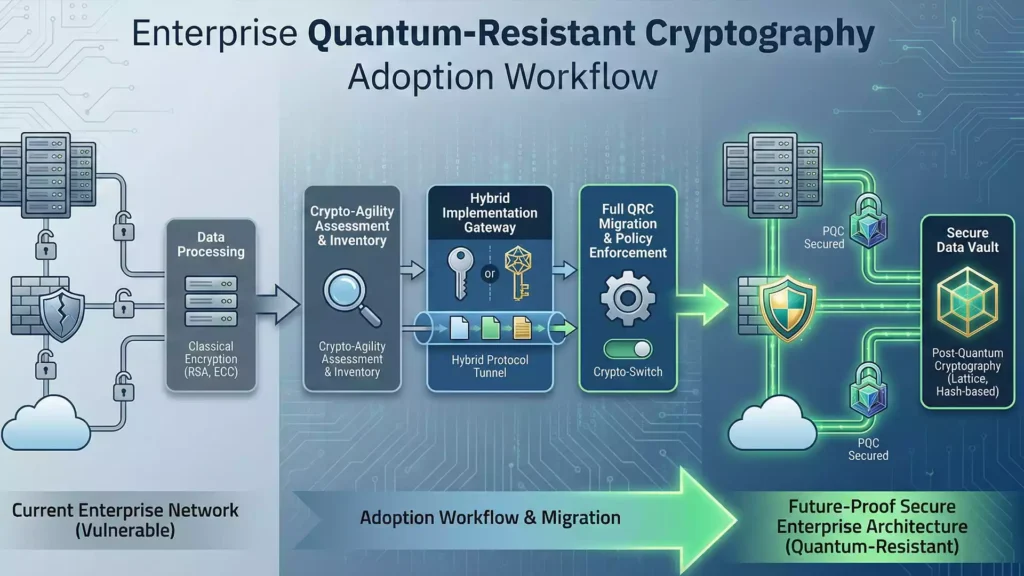
The digital security landscape is shifting rapidly this year. Quantum-resistant cryptography adoption has emerged as a critical priority for forward-thinking enterprises. Traditional encryption methods are becoming vulnerable to powerful new computing systems. Therefore, businesses must act now to protect their sensitive information from future decryption attacks.
Industry leaders effectively call this the “Harvest Now, Decrypt Later” threat. Attackers steal encrypted data today, waiting for quantum computers to break it later. Consequently, implementing quantum-resistant cryptography adoption strategies immediately is the only viable defense.
Experts at IT TOUCH (https://ittouch.io/services/cybersecurity) help organizations navigate this complex transition. We assess your current risk levels. Furthermore, we design roadmaps that align with evolving global standards.
Implementing Post-Quantum Security Standards
Regulatory bodies are finally finalizing their guidelines. The NIST (National Institute of Standards and Technology) has released confirmed algorithms for general use. Adhering to these post-quantum security standards ensures your infrastructure remains compliant and secure.
Transitioning is not a simple “flip of a switch.” It requires a hybrid approach initially. Systems must support both classic and new encryption methods simultaneously. This phase prevents service disruptions during the upgrade process. Our consulting team (https://ittouch.io/services/consulting) specializes in managing these delicate migrations.
Moreover, major tech firms like IBM Quantum are already integrating these protocols. They understand that trust is the currency of the digital age. Thus, failing to upgrade could result in significant reputational damage.
Achieving Cryptographic Agility Solutions
Static security measures are no longer sufficient. You need cryptographic agility solutions to survive in 2026. This approach allows you to switch encryption methods quickly without rewriting applications. Therefore, if a specific algorithm is compromised, you can pivot instantly.
This agility is a core component of modern infrastructure management (https://www.google.com/search?q=https://ittouch.io/solutions/infrastructure). It empowers your IT teams to react to threats in real-time. Additionally, agencies like CISA emphasize agility as a cornerstone of cyber resilience.
We recommend reading our detailed blog posts (https://ittouch.io/blog) for technical deep dives. Staying informed is your first line of defense. Also, consider how future-proof data protection impacts your bottom line.
Preparing Your Organization Today
Do not wait for a quantum breach to make headlines. Start your quantum-resistant cryptography adoption journey today. Review your data inventory. Identify long-term secrets that need immediate protection.
Check out The Quantum Insider for the latest industry news. They track the speed of hardware advancements closely. Similarly, MIT Technology Review offers excellent insights into the timeline of these technologies.
If you are unsure where to begin, contact us (https://www.google.com/search?q=https://ittouch.io/contact-us). We are ready to secure your digital future. Together, we can build a fortress that stands the test of time.
Relevant Video: For a deeper understanding of the security landscape in 2026, watch this insightful discussion: Cybersecurity Trends in 2026. This video explains how quantum mechanics and other emerging technologies are reshaping data protection strategies this year.